How many types of virtualization available in this technology?
There are two types of virtualization available:
- Type 1 Virtualization
- Type 2 Virtualization
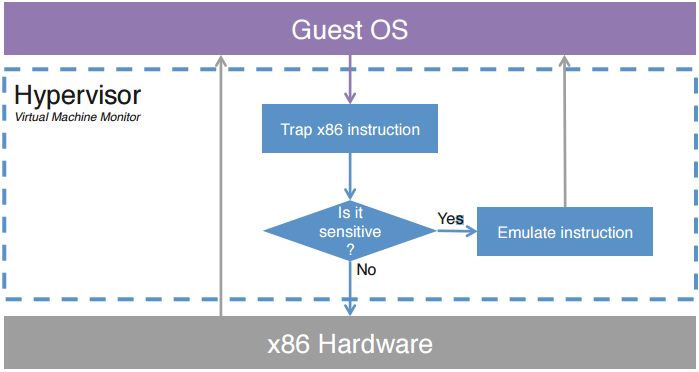
The type 1 virtualization has a Guest OS, which traps x86 instruction and determines if the instruction is sensitive or not. If it is sensitive, it emulates instruction to Guest OS. And if it is not sensitive, it is sent to x86 Hardware.
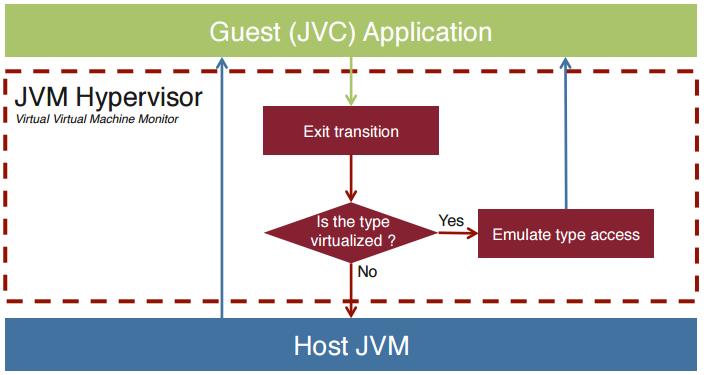
So, how do developers bring complete isolated virtualization for Java?
The Waratek hypervisor exposes control access and monitoring through the Java Virtual Interface. Through this step, many things get enable:
- Visibility of all type of access
- Type emulation
- Type Sharing
Securing the application is the next step
If the security landscape is too hot, there will be risks to applications, departmental silos issues and huge amounts of efforts will be required. If the security landscape is too cold, there will be data exposure and low knowledge of app logic.
Inside the application, there should be code reviews, static analysis, and team training. For this, an approach will allow developers to get into the framework and application and do in a politically and operationally practical way.
Inside infrastructure, there are the web and next-gen firewalls, intrusion prevention, and agent-based.
Benefits of Security:
- There will be application threat monitoring and forensics
- There will be legacy java app protection and compliance
Do you know? JVMs are also insecure.
The JVM itself performs No security tests. All enforcement is through the Security manager and Java API’s level. If these are bypassed or compromised, the JVM can be instructed to do ANYTHING.
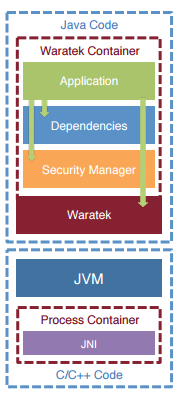
Waratek technology monitors all operations
The Waratek layer checks every call the dependent libraries of the app and the app itself need to make. Waratek inspects the calls against the rules and logs the suspicious behavior (if any). Developers can also isolate untrusted JNI code by separating the library within its process container at the Operating System Level. It is very low latency as everything is local to the JVM.
There are language rules, Input-Output rules, and other rules that cover all aspects of the application. We will discuss them now!
Language Rules are:
- Class loading – Class or package level
- Class linking – Any defined class
- Throwable – exception classes
- Reflection – from variable to package level
Input-Output rules are:
- Network – any network I/O
- File – Any file I/O
Other rules are:
- Process forking – starting external processes
- Native code – accessing JNI
Legacy Java is among big and expensive issues
Almost 93% of the companies are running Java versions over 5 years old. The average company has distinct 51 Java versions with less than 1% of installed Java is up-to-date.
Applications need to be re-tested if migration is needed. In some cases, there will be a requirement of module rewrites.
How legacy containers enhance the life of the application? What are the benefits of the legacy java approach?
Legacy Java approach has two major benefits:
- There will no change in the application
- Externally the world can move on
The application doesn’t see any change of API. There are still unopened calls, and a series of objects still run. The app still uses APIs, against which the first test done. The surrounding infrastructure, an updated and the administration is on an updated supported platform.
Infrastructure benefits of virtualization
- Drive up data center density to lower the working cost and future capital cost.
- Manage resources of app live for greater stability and uptime
JVM memory is inflexible, and Waratek enhances stability. With access to free memory, every application has a higher effective memory. Waratek also brings a feature to its Java-protection platform that enables upgrading to the latest Java version without any need of installing Java updates or touching the apps running inside the JVM.
The updated version of its app security for Java employs secure virtual containers around the Java application stack to apply the performance and security features of the latest Java 8 platform’s security and performance levels without installing Java 8. App security for Java is a RASP platform container with a rules engine that brings the security features of the updated Java version to protect the application.
How the technology Waratek fixes security flaws automatically in Java apps?
The latest features cut the need to make any changes to the code, and can cut the time consumed to remediate flaws from three months to thirty minutes! With the help of assessments developed by software app security testing tools, Waratek can automatically generate rules. These rules offer a virtual patch against code level attacks, including unrestricted uploads, SQL injection, path traversal, command injection, code injection, etc.
Waratek’s new security app RASP can use assessments, software app security testing tools and automate virtual patching. This core job requires testing and evaluation of the applications to find the vulnerabilities. Fixing these vulnerabilities is a manual and time-consuming process. At a typical company, only a fraction of the vulnerabilities determined in internally written apps fixed. For apps and software components offered by third-parties, the number is higher.
This article is shared by Java Developers India team to understand about the use and benefits of the Waratek technology. If you need, more information, you can contact the experts today.
Read Related Articles:
Is shortage of skilled Java experts is a concern for the future?
Top 5 emerging practices for real-time data integration

 RSS Feed
RSS Feed
